How to properly store encryption key images are ready in this website. How to properly store encryption key are a topic that is being searched for and liked by netizens today. You can Find and Download the How to properly store encryption key files here. Get all free vectors.
If you’re searching for how to properly store encryption key images information related to the how to properly store encryption key keyword, you have pay a visit to the right blog. Our site frequently provides you with hints for seeking the highest quality video and picture content, please kindly surf and find more informative video content and images that match your interests.
How To Properly Store Encryption Key. It will use the password to generate the encryption key and use that key from then on without storing it. 07052019 You would need to provide the password to your web server every time you start it since it isnt stored anywhere. How to sort a list of dictionaries by a value of the dictionary. Grant read permissions only to the group of users that are allowed to use the password.

 The Definitive Guide To Sql Server Encryption And Key Management From info.townsendsecurity.com
The Definitive Guide To Sql Server Encryption And Key Management From info.townsendsecurity.com
It will use the password to generate the encryption key and use that key from then on without storing it. How to get the Cartesian product of a series of lists. You then ask AWS to decrypt the encrypted data key using the master key AWS maintains this gives you the original data key. When you start a SQL Server instance the SQL Server database calls the EKM Provider software to. Probably the best thing you can do is this. 25072019 To decrypt data all you need to do is take the encrypted message and break it into two pieces.
- If you can apply meaningful ACLs to the file that stores the value then do so.
You have to decide what is an acceptable level of risk. It will use the password to generate the encryption key and use that key from then on without storing it. These approaches are platform-agnostic. - Used the ProtectedData class to encrypt the value as stored on disk. Websites have SSLTLS certificates containing the public key while the private key is installed on the websites origin server or CA. 30092019 The encrypted database key is then stored locally on disk in the SQL Server context.

 Source: docs.mongodb.com
Source: docs.mongodb.com
It would have cost less than a penny to add a hardware core if you had a custom IC. Grant read permissions only to the group of users that are allowed to use the password. 15022019 You can store your private keys in a cryptomator secured directory and have it encrypted in real time with your cloud provider. You then ask AWS to decrypt the encrypted data key using the master key AWS maintains this gives you the original data key. 05042009 That way you dont have to store the key or at least any keys whether they are symmetric or private keys can be encrypted with this bootstrap.
 Source: documentation.suse.com
Source: documentation.suse.com
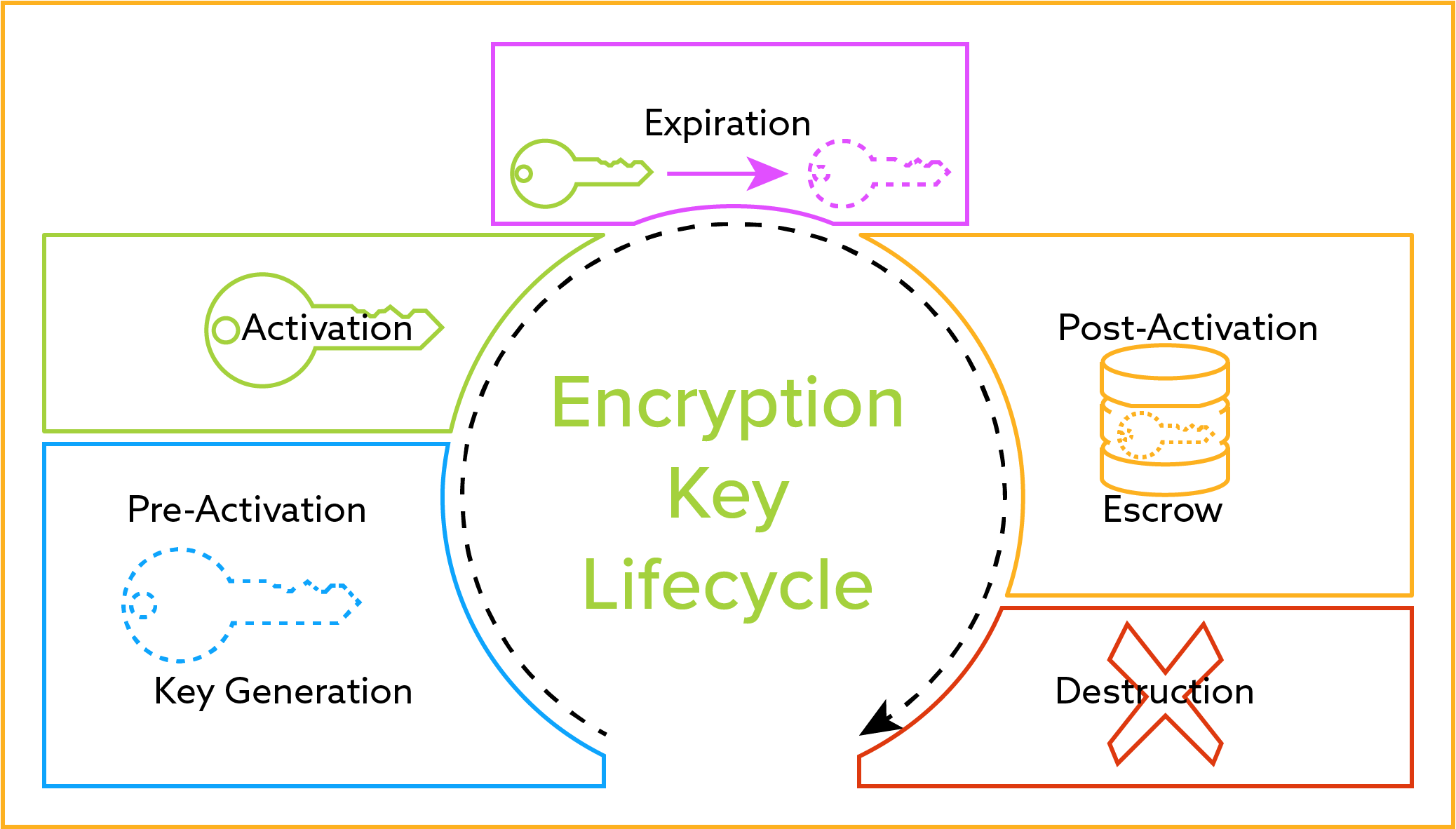
Public key cryptography is vital for Secure Sockets Layer SSL and Transport Layer Security TLS which are themselves vital for secure HTTPS web browsing. How to properly store an encryption key. The encryption key is created and stored on the key management server. The key rotation period should depend on your needs. How to sort a list of dictionaries by a value of the dictionary.
 Source: pinterest.com
Source: pinterest.com
The encryption key is created and stored on the key management server. There is no safe. 06062017 With your constraints there is no way to safely store keys and this is from a hardware perspective. To safely store your data in a database youd start by generating a strong secret key. It will use the password to generate the encryption key and use that key from then on without storing it.
 Source: info.townsendsecurity.com
Source: info.townsendsecurity.com
You then ask AWS to decrypt the encrypted data key using the master key AWS maintains this gives you the original data key. 05082018 Expecting the compromise of E it would be a good idea to periodically rotate keys and move old keys away from E to safe offline storage so any incident wont affect files encrypted with previous keys. You have to decide what is an acceptable level of risk. How to convert DateTime to Unix timestamp and vice versa in C. It would have cost less than a penny to add a hardware core if you had a custom IC.
 Source: aws.amazon.com
Source: aws.amazon.com
How to sort a list of dictionaries by a value of the dictionary. How to convert DateTime to Unix timestamp and vice versa in C. How to get the Cartesian product of a series of lists. 20082014 Otherwise it would be easy to find all the common data in a database and deduce a pattern from the encryption. Probably the best thing you can do is this.
![]() Source: thesslstore.com
Source: thesslstore.com
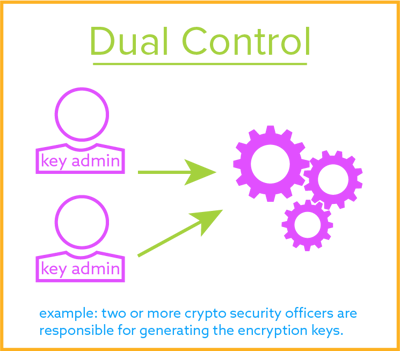
It will use the password to generate the encryption key and use that key from then on without storing it. If not store your secret key in a file by itself and modify its permissions to make it accessible only to the user running the web application. The encrypted data key and the encrypted data. The key can be created by a sole administrator or through dual control by two administrators. Websites have SSLTLS certificates containing the public key while the private key is installed on the websites origin server or CA.
 Source: thesslstore.com
Source: thesslstore.com
A cryptocurrency wallet is a software program designed to store your public and private keys send and receive digital currencies monitor their balance and interact with various blockchains. A cryptocurrency wallet is a software program designed to store your public and private keys send and receive digital currencies monitor their balance and interact with various blockchains. - If you can apply meaningful ACLs to the file that stores the value then do so. The encrypted data key and the encrypted data. How to convert DateTime to Unix timestamp and vice versa in C.
 Source: docs.mongodb.com
Source: docs.mongodb.com
Finally you decrypt the encrypted data using the data key that you just decrypted. 05042009 That way you dont have to store the key or at least any keys whether they are symmetric or private keys can be encrypted with this bootstrap. How to sort a list of dictionaries by a value of the dictionary. The encrypted data key and the encrypted data. The key manager creates the encryption key through the use of a cryptographically secure random bit generator and stores the key along with all its attributes into the key storage database.
 Source: medium.com
Source: medium.com
Websites have SSLTLS certificates containing the public key while the private key is installed on the websites origin server or CA. I have done a bit of encryption of data in the past and just stored my encryption key in applicationcfc. How to safely store encryption key in a NET assembly. If the risk of someone using reflector or just opening up the assembly using the SystemReflectionAssembly class and. 05082018 Expecting the compromise of E it would be a good idea to periodically rotate keys and move old keys away from E to safe offline storage so any incident wont affect files encrypted with previous keys.
 Source: pinterest.com
Source: pinterest.com
The key rotation period should depend on your needs. Finally you decrypt the encrypted data using the data key that you just decrypted. 30092019 The encrypted database key is then stored locally on disk in the SQL Server context. How to convert DateTime to Unix timestamp and vice versa in C. 05042009 That way you dont have to store the key or at least any keys whether they are symmetric or private keys can be encrypted with this bootstrap.
 Source: docs.mongodb.com
Source: docs.mongodb.com
How to read inputs as numbers. It will use the password to generate the encryption key and use that key from then on without storing it. The key rotation period should depend on your needs. You then ask AWS to decrypt the encrypted data key using the master key AWS maintains this gives you the original data key. - Used the ProtectedData class to encrypt the value as stored on disk.

This site is an open community for users to share their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site serviceableness, please support us by sharing this posts to your preference social media accounts like Facebook, Instagram and so on or you can also bookmark this blog page with the title how to properly store encryption key by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.